Building a Winning Cybersecurity Strategy
Get Your Copy Now

Building a Winning Cybersecurity Strategy
ESM provides today’s IT Security Leaders with insights and considerations for building a winning cybersecurity program that aligns with organizational business drivers.
![]() Help guide IT security leaders through a checklist of best practices for building a successful Cybersecurity framework
Help guide IT security leaders through a checklist of best practices for building a successful Cybersecurity framework
![]() Learn how to align the Cybersecurity management plan with your organization's strategy and goals
Learn how to align the Cybersecurity management plan with your organization's strategy and goals
![]() Establish a cross-functional governance structure for your Cybersecurity program
Establish a cross-functional governance structure for your Cybersecurity program

Building a Winning Cybersecurity Program
Part 1
- Help guide IT security leaders through a checklist of best practices for building a successful Cybersecurity framework
- Learn how to align the Cybersecurity management plan with your organization's strategy and goals
- Establish a cross-functional governance structure for your Cybersecurity program
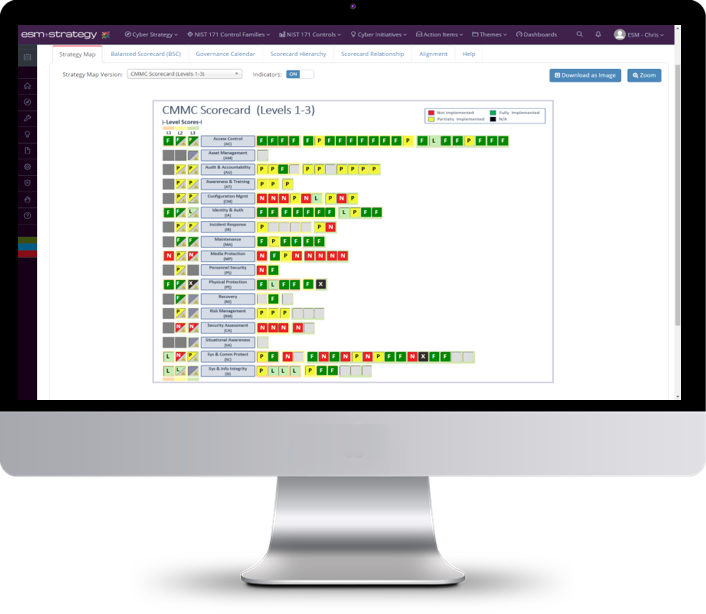
ESM Cybersecurity provides a data-driven view of our cybersecurity compliance posture giving me the confidence knowing that we have both a solid cybersecurity strategy and repeatable, efficient approach to ongoing compliance.
.png)
Leading organizations trust ESM






Confidently Manage your Cybersecurity Program
By starting with a Cyber Strategy Map your leadership team will be able to communicate their vision with actionable objectives helping employees stay focused and improving results.
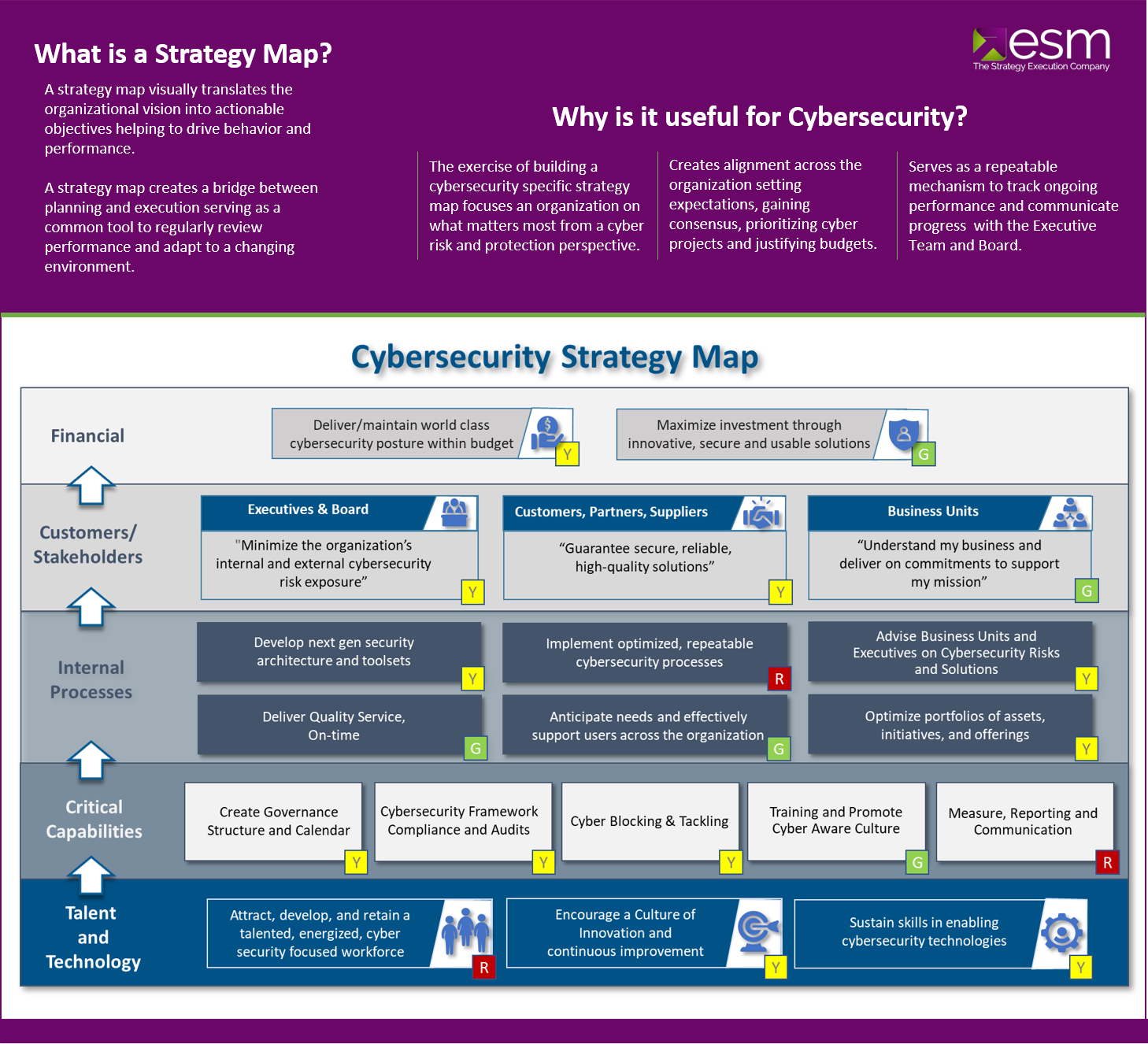
Gain control with ESM Cybersecurity
Say goodbye to complex spreadsheets and exhausting slide deck creation. With ESM, your strategic and compliance standing are tracked in one integrated solution.
- Formulate and create your compliance-based strategy.
- Rapidly operationalize multiple Compliance Frameworks (NIST, CMMC, ISO, PCI DSS, GDPR)
- Standardize your Cybersecurity Processes
- Close the Gaps between Current State and Target State
- Communicate Results with Key Stakeholders