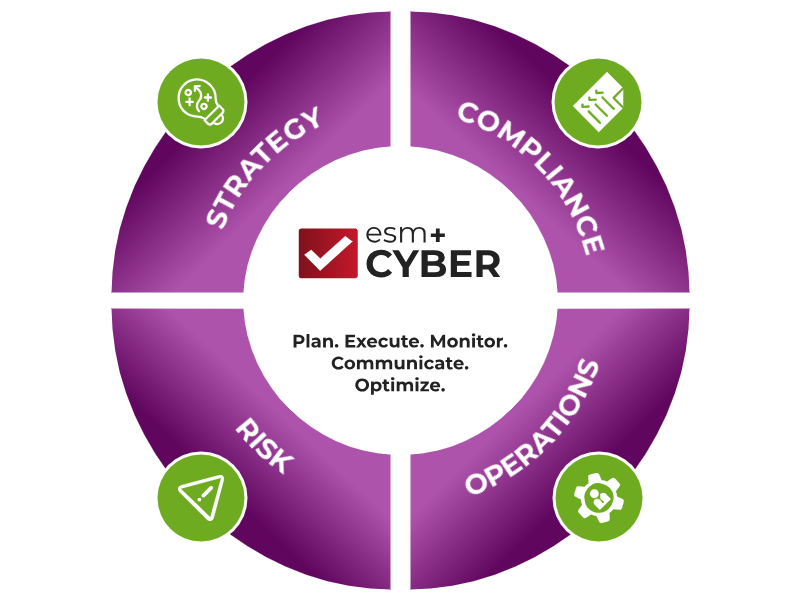
GAIN CONTROL OF YOUR CYBERSECURITY PROGRAM WITH ESM+CYBER
ESM+Cyber allows for organizations to continuously evolve their cybersecurity program, track and communicate changes, mature, and improve their overall cybersecurity stance.
![]() Cybersecurity Strategy: align business objectives, risk tolerance, access requirements and budget
Cybersecurity Strategy: align business objectives, risk tolerance, access requirements and budget
![]() Cybersecurity Compliance: track any compliance framework, prepare for audits and demonstrate your compliance posture
Cybersecurity Compliance: track any compliance framework, prepare for audits and demonstrate your compliance posture
![]() Cybersecurity Operations: prepare cyber plans, layout operational calendars and track progress on cybersecurity projects
Cybersecurity Operations: prepare cyber plans, layout operational calendars and track progress on cybersecurity projects
![]() Cybersecurity Risk: track risks in an interactive risk register, visualize risk score in risk matrices and prioritize treatment
Cybersecurity Risk: track risks in an interactive risk register, visualize risk score in risk matrices and prioritize treatment

An Effective Cybersecurity Program Requires More Than a Checklist!

Cybersecurity Strategy
Align business objectives, risk tolerance, access requirements and budget.

Track Cybersecurity Compliance
Track any compliance framework and demonstrate you’re actively addressing cybersecurity risk.
Manage projects to reduce cyber risk
Prepare cyber plans, prioritize and track progress on projects designed to improve cybersecurity posture.

Continuously measure performance
Measure key security metrics and trend performance over time.
Cybersecurity review meetings
Disciplined, repeatable approach to ongoing reviews and communication with board-ready outputs.
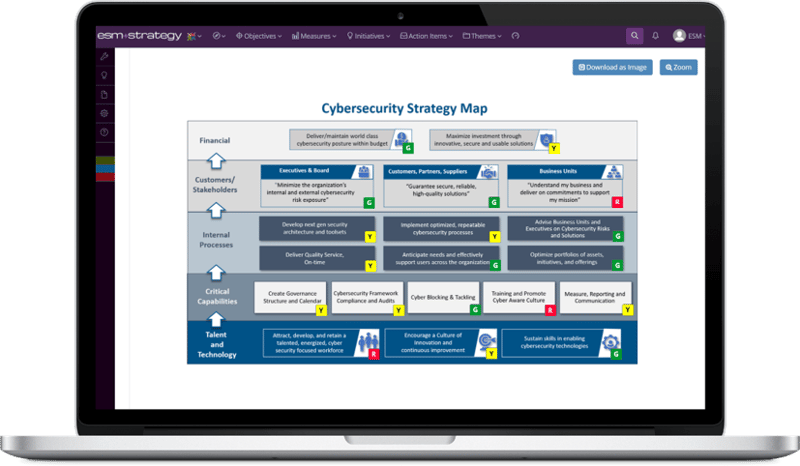
Formalize, Communicate and Track Cybersecurity Strategy
Create a one-page cyber strategy map to capture objectives, set direction and communicate with team
Assign ownership and define metrics that demonstrate performance
Enter scores, metrics, and analysis on an agreed to timeline
Review performance on a regular cadence with drill downs into objectives, metrics and projects
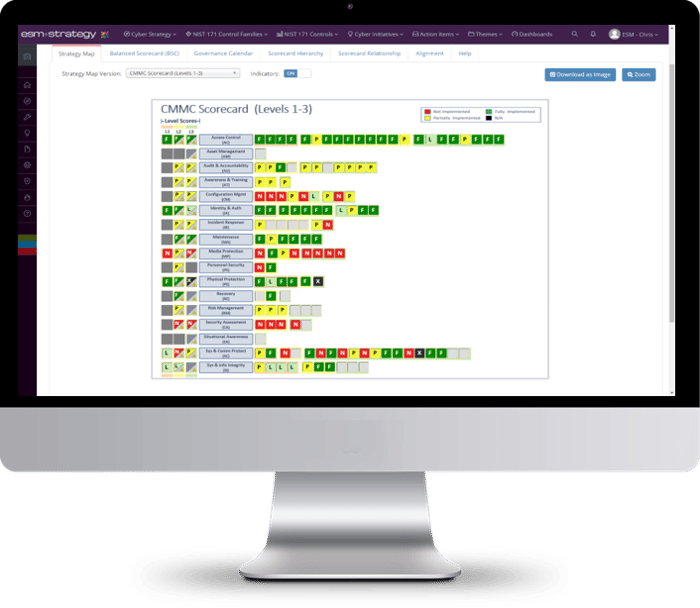
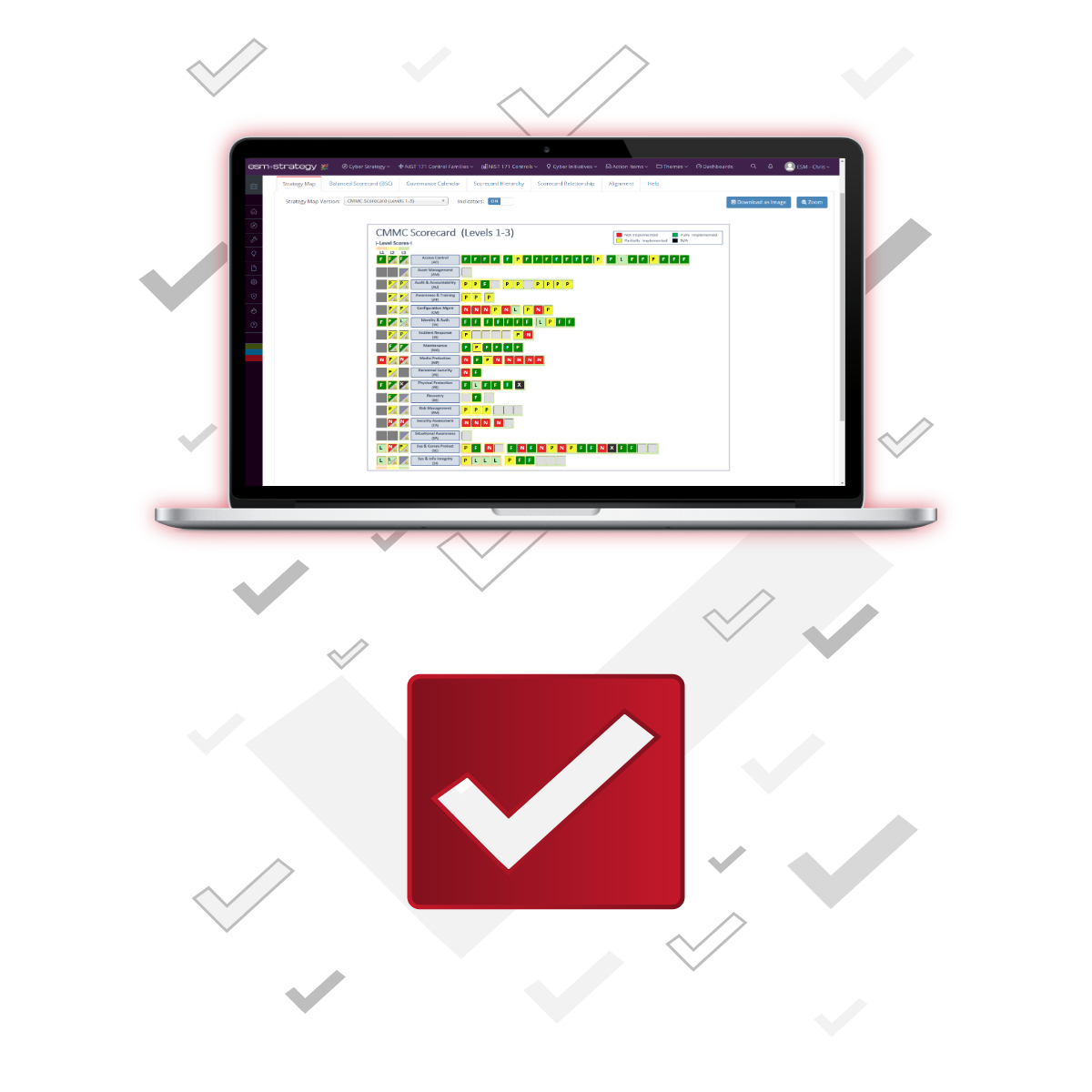
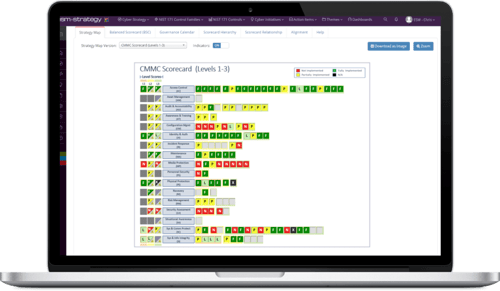
Manage Cybersecurity Compliance
ESM Cyber supports multiple compliance frameworks including NIST CSF, NIST Privacy, NIST 800-171, CMMC, ISO 27001 or your own custom framework.
Choose a cybersecurity framework(s) and tailor it to your specific needs
Track scores & maturity across control families and controls over time
Centralize documentation: evidence, reports, policies, procedures, budgets, POA&Ms and more.
Quickly prepare for compliance audits and board meetings with one click reporting
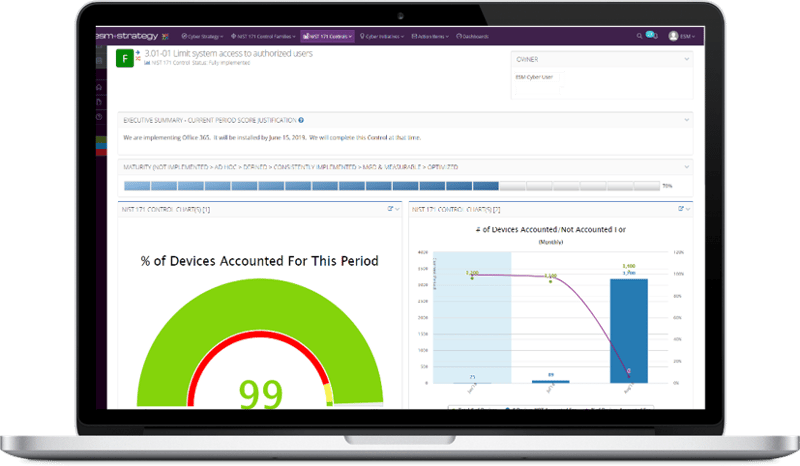
Continuously measure and communicate performance
Quickly generate point-and-click strategy, operations and compliance reports that demonstrate progress on cybersecurity initiatives and your ongoing cybersecurity posture.
ESM +Cyber has drag-n-drop dashboards, canned reports and custom reports to help you answer critical business questions.
Are we meeting strategic objectives?
Are we compliant? What is our maturity level?
Are we above or below our cyber-security KPI targets?
What initiatives are ahead or behind schedule?
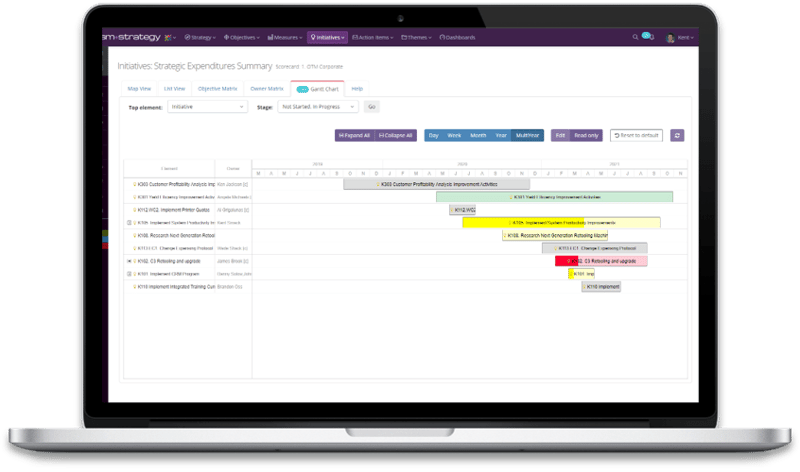
Prioritize, Track and Execute Cybersecurity Projects & Activities
It's hard to pick which projects you should invest in to improve your cybersecurity posture and even more difficult to manage all the moving parts. We want to help make that a little bit easier.
Prioritize and manage cybersecurity initiatives all in one tool.
Standardize your evaluation framework for cybersecurity investments.
Create initiatives, assign ownership, track budgets, and monitor ongoing progress.
Confidently run productive cybersecurity review meetings
Let's face it, the executive team isn't an easy audience. They need to be informed, but only with pertinent info.
Create a repeatable approach that draws attention to what matters most to the executives and that doesn't overburden your team.
Performance review and analysis completed in advance
Meeting focus: risks, projects, outcomes, and opportunities to improve
Start high level and deep dive where necessary
Drive actions: follow-up items, due dates, responsibility, notifications
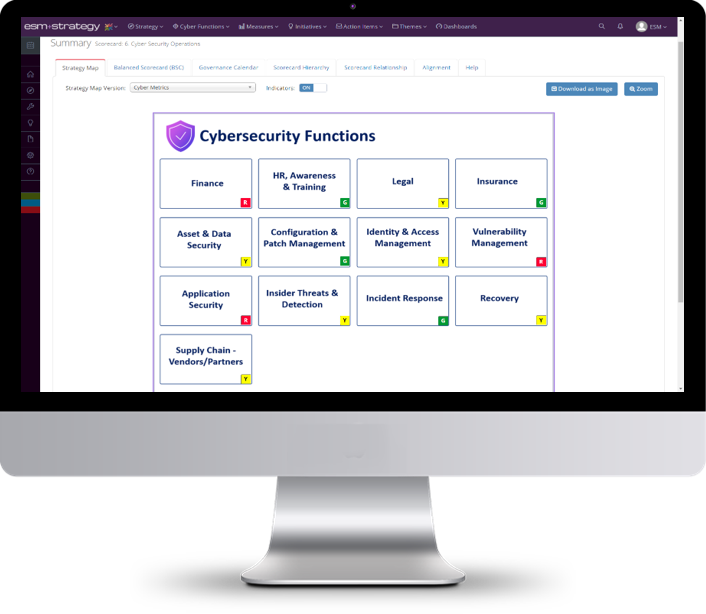

Who can benefit from ESM+CYBER?
How We Help Government Contractors
ESM Cybersecurity helps Government Contractors manage your overall cybersecurity program with confidence all in a centralized application, across customers with unique requirements. Doing so has many benefits:
- Don’t lose business with current accounts due to NIST 800-171 or CMMC compliance shortcomings.
- Win new business by highlighting a disciplined and repeatable approach to ongoing cybersecurity compliance.
- Prove to government customers you are compliant through point-and-click compliance reports, online POA&Ms, reporting on progress of cybersecurity initiatives and cybersecurity hygiene practices, and ongoing monitoring of your cybersecurity posture.
- Manage your technology vendors and projects more efficiently and effectively through the use of a centralized execution tool.
- Align your investments in cyber to the areas most valuable to address NIST 800-171 and CMMC shortcomings.
- Prove your worth and take the lead in prime contractor and government customer cybersecurity review meetings.
We’d welcome the opportunity to walk you through the ESM Cybersecurity application or to jump on a call to learn more about your cybersecurity needs to see if we might be a good fit for your organization.

Commercial Enterprises
Centralize cybersecurity strategy, compliance and implementation in one tool.
Read moreHow we Help Commercial Enterprises
ESM Cybersecurity gives commercial enterprises a centralized tool to manage your overall cybersecurity program with confidence. Whether it’s the NIST Cybersecurity Framework, another popular framework, or a homegrown framework that you are striving to follow, ESM Cybersecurity helps you:
- Formulate a cybersecurity strategy that aligns your organizational objectives and risk tolerance with target maturity levels and budgetary constraints.
- Create an ongoing governance calendar surrounding cyber hygiene blocking and tackling, strategic initiative management and tracking.
- Identify the most critical cybersecurity gaps, establish a roadmap with the prioritized initiatives required to close the gaps and track ongoing progress and impact of those initiatives on overall cybersecurity posture over time.
- Collaborate with extended team, assign accountability, and quickly generate board-ready and operational reports for internal and external stakeholders.
We’d welcome the opportunity to walk you through the ESM Cybersecurity application or to jump on a call to learn more about your cybersecurity needs to see if we might be a good fit for your organization.

Government Agencies
Centralize your cybersecurity strategy, oversight and implementation in one tool.
Read moreHow we Help Government Agencies
The General Accounting Office (GAO) recently identified “Ensuring the Cybersecurity of the Nation” as a high risk priority , stating that “Federal agencies and other entities need to take urgent actions to implement a comprehensive cybersecurity strategy, perform effective oversight, secure federal systems, and protect cyber critical infrastructure, privacy, and sensitive data.”
ESM Cybersecurity serves as the overarching umbrella to manage your Agency’s cybersecurity program:
- Formulate a cybersecurity strategy that aligns your organizational objectives and risk tolerance with target maturity levels and budgetary constraints.
- Create an ongoing governance calendar surrounding cyber hygiene blocking and tackling, strategic initiative management and progress tracking.
- Identify the most critical cybersecurity gaps, establish a roadmap with the prioritized initiatives required to close the gaps and track ongoing progress and impact of those initiatives on overall cybersecurity posture over time.
- Collaborate with extended team, assign accountability, and quickly generate board-ready and operational reports for internal and external stakeholders.

Cybersecurity Consultants
Standardize the delivery of your cybersecurity assessment and implementation services.
Read moreHow we Help Cybersecurity Consulting Firms
As a trusted advisor responsible for assessing numerous organizations’ cybersecurity posture and compliance, you need a tool that captures your unique approach to cybersecurity services (compliance, strategy and execution) while making it an easy and repeatable process for your team to deliver on an ongoing basis.
ESM Cybersecurity is that tool. Ensuring your customers have a strong cybersecurity posture requires more than a one-time check list.
- Capture and formulate cybersecurity strategies for your customers based on their unique business goals, overarching strategy, risk tolerance and budget.
- Track compliance, strategy and execution for all of your customers in one easy to use tool.
- Generate “Board Ready” Assessments and Reports with the click of a mouse.
- Prioritize strategic initiatives and projects based on customer needs.
- Reduce rework, manual processes, and enhance the productivity of your team with a repeatable framework for cybersecurity assessments and services delivery.
- Create an ongoing relationship with customers using a tool that fosters communication and recurring check-ins.
We’d welcome the opportunity to walk you through the ESM Cybersecurity application or to jump on a call to learn more about your cybersecurity needs to see if we might be a good fit for your organization.

How we Help 3CPAOs
We make it easier for C3PAOs to complete assessments for their customers.- Leverage a customer's current NIST 800-171 control level assessment and map to CMMC domains and practices to save time
- Produce Board Ready Reporting with the click of a mouse
- Track maturity at a practice level and rollup to domains
- Track Levels 1-3, 1-4, 1-5 based on your customer's desired level....


DON'T TAKE OUR WORD FOT IT. LISTEN TO WHAT OUR CUSTOMERS ARE SAYING.
ESM Cybersecurity provides a data-driven view of our cybersecurity compliance posture giving me the confidence knowing that we have both a solid cybersecurity strategy and repeatable, efficient approach to ongoing compliance.
-1.png)

WHY ESM+CYBER?
 20 years of success
20 years of success
20 years of success implementing strategic solutions.
 World class customers
World class customers
World class customers in government, finance, healthcare, utility, retail, manufacturing, insurance, and education across the globe rely on ESM to execute their strategy and drive results.
 Flexible solutions
Flexible solutions
Our cloud-based solution is rapidly implemented and tailored to your specific needs. Or, ask us about our on-premise solutions if that's a better fit for you.
 Cybersecurity frameworks built in
Cybersecurity frameworks built in
NIST CSF, NIST 800-171, NIST Privacy Framework, NIST 800-53, DoD Cybersecurity Maturity Model Certification (CMMC), ISO 27001, or your own internal custom set of control families and controls.
FEATURES / FUNCTIONALITY
Get control of your Cybersecurity Program
CONTINUOUS COMPLIANCE MONITORING
Understand your compliance status based on NIST centered or other cybersecurity frameworks.
CYBERSECURITY ROADMAP
Establish a roadmap and POAM to help close the gaps in your current compliance.
PROJECT/TASK PRIORITIZATION
Prioritize your initiatives based on risk tolerance, business objectives and budget. Then assign to key stakeholders to execute.
ADVANCED DATA HANDLING
Seamlessly incorporate data from spreadsheets or from other systems.
SELF ASSESSMENT QUESTIONNAIRES
Use framework guidance questions, leverage your Auditors assessment or create your own internal questions based on your unique business requirements.
POA&M GENERATOR
Generate and share your POA&M with initiatives, dates, and budget right out of the system.
DASHBOARDS & REPORTS
Answer key business questions using canned reports or generate custom reports and dashboards on the fly.
GOVERNANCE CALENDAR
Track initiatives, tasks, and milestones on a centralized shared calendar.
BUDGET TRACKING
Track budget, forecast and actual spend across strategic initiatives.
ALERTS & NOTIFICATIONS
Notify users when information requires updates, deadlines are approaching and when metrics are out of tolerance.
KNOWLEDGE MANAGEMENT
Store critical information in a centralized repository: Security Plans, Policies and Procedures, Budget and Forecasts, Operational Reports, Other Evidence.
CHOOSE YOUR FRAMEWORK OR CUSTOMIZE YOUR OWN
Use popular frameworks (NIST, CMMC, ISO 27001), expand with custom controls and track your ongoing compliance and cybersecurity posture

EASILY MANAGE YOUR CYBERSECURITY PROGRAM AND COMPLIANCE FRAMEWORK
Develop your cybersecurity strategy using best practice tools and templates. Customize for your industry and company needs. Monitor cybersecurity maturity with score tracking and controls. Easily prepare for audits and board meetings with centralized reports.

Free to start. Unlimited users.
Ready to see ESM+Cyber in action?
Our team of experts will happily schedule a time to talk with you and show you a live, private demo.
|
|