Cybersecurity Breaches Infographic
Get Your Copy Now

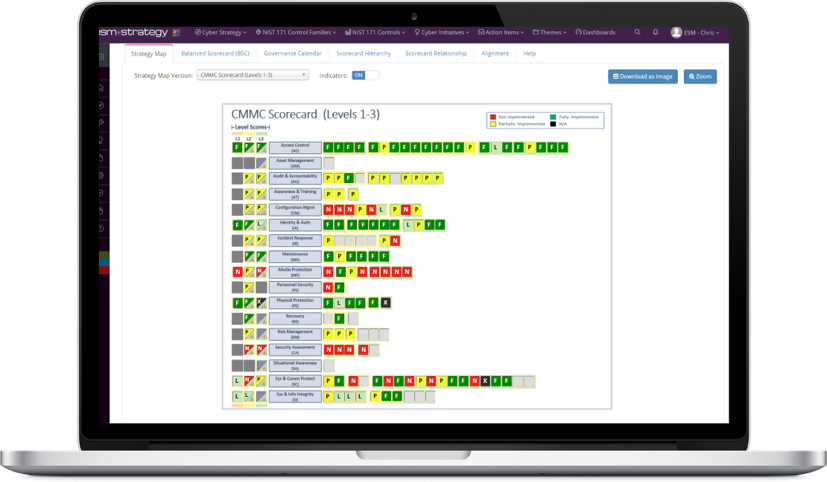
Risks, Benefits, Impact, and Costs of Different Cybersecurity Approaches
Which approach is best with regard to breaches?
Many organizations fail to fully realize the impact a cybersecurity breach would have on their business. Cybercriminal cause more problems than just stolen data.
- Is your cybersecurity program reactive? Or Proactive? Both?
- How much does a breach cost?
- In what other ways does a breach negatively impact your business?
Building a Winning Cybersecurity Program
Part 1
- Help guide IT security leaders through a checklist of best practices for building a successful Cybersecurity framework
- Learn how to align the Cybersecurity management plan with your organization's strategy and goals
- Establish a cross-functional governance structure for your Cybersecurity program
Leading organizations trust ESM





GAIN CONTROL OF YOUR CYBERSECURITY PROGRAM WITH ESM+CYBER